In 2003, WordPress initially made its introduction as a basic blogging tool, and only a few people were aware of this software’s existence. But, over the years, the developers have made significant improvements and converted WordPress into a robust Content Management System.
It’s one of the most accessed website building applications that developers use for plug-in, theme, and widget creation. WordPress comes with an easy user interface which attracts 400 million people to use this website daily.
Researchers stated that currently, 64 million websites are using WordPress. And, it can be assumed that you have also created an account on this website development site. For using easy-to-assume credentials, your WordPress can become vulnerable to data threats. Once the cyber attackers acknowledge the credentials, you might have to face adverse consequences.
These hackers can even change the website’s content and upload that to the corresponding websites. When Google finds out misleading or improper information, it will automatically remove the website. And, this sort of instance will negatively affect the business’s reputation and revenue.
Though WordPress is widely known as one of the safest platforms, you have to still make sure it’s secure enough. But before discussing the security measures, here we are mentioning the common WordPress credential-hacking methods:
1. Shoulder Surfing

You must have heard about this credential-stealing method before. Shoulder surfing attacks take place when someone intentionally tries to check and gather WordPress-related information; they track the user’s movement. For instance, if an employee has recently seen you typing WordPress’s credentials, then he might use that information.
Shoulder surfing can occur in any public place. So, you have to be extremely careful while providing the login credentials of WordPress while you’re travelling.
Consider using a privacy screen to block the screen visibility, reducing the possibility of experiencing shoulder surfing. You can contact the top-ranked WordPress development experts to get more recommendations.
2. Phishing Attack

Recently, Wordfence, the security plugin of WordPress, blocked more than 90 million malicious login attempts. And, these repetitive login attempts were made from 57 million different IP addresses. Do you know more than 2,800 phishing attacks occur per second in WordPress? Yes! In this CMS platform, plug-in plays an important role, and most of the breaching activities take place through these.
Usually, the cyber attackers craft an email so that it will look like it came from a legitimate source. And, when the users open the email attachment, it can provide the hackers with sensitive web-based application credentials.
Spear phishing is another effective credential-stealing method that cyber attackers mostly use. However, phishing emails can even come from trusted sources, such as via a coworker. So, once you receive any suspicious mail, make sure to verify its authenticity. We would highly recommend not sharing any WordPress credentials with anyone.
Phishing Scams can even Trick WordPress Developers!
Those who manage multiple WordPress sites often receive emails from WordPress. So, when the email gets bombarded with emails, it becomes challenging to identify the legitimate one. And, sometimes, the scammers forward an email, so it can look like an actual person has sent it. So, every recipient should check twice before opening any WordPress-associated email.
3. MitM (Man-in-the-Middle Attack)
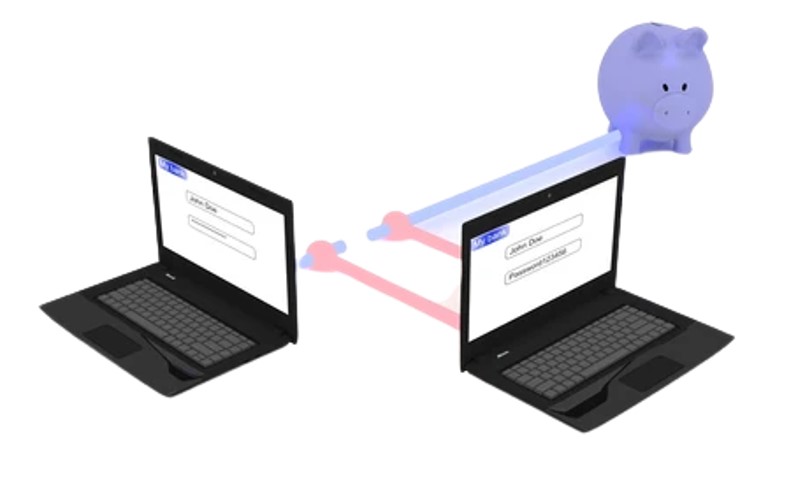
Through man-in-the-middle attack format, the attackers can easily take control of the WordPress website. Usually, in this type of credential breaching technique, the hackers act as an intermediary between the sender and the recipient. By continually monitoring or modifying the traffic, they try to reach out to both these parties’ servers. Man-in-the-middle attacks are mostly used for stealing login credentials or other website-related information.
Though this sort of cyberattack can occur anytime, fortunately, it’s easily preventable. Make sure the website you are accessing and its SSL/TCL certificates are valid. Google always notifies the users while accessing any website that the SSL expired. Avoid opening those sites, which can increase the data breaching vulnerability of the WordPress site. You can also switch to Virtual Private Network from a public network to prevent unauthorised users from accessing WordPress credentials.
4. Credential Stuffing

Credential stuffing occurs when the hacker already has somehow managed to obtain the WordPress-related credentials. Nowadays, this type of cyber attack has become the major cause of data breaches. Because it was found that almost 65 per cent of users uses the same password on multiple WordPress accounts.
In credential stuffing, the attackers use bots for sending automated requests containing the WordPress username and password. And, after the user’s confirmation, the hackers get into the WordPress account using the pre-assumed credentials to steal information.
Do you know what could be the best way to prevent credential stuffing attacks? Yes! Don’t use the same password or username on different WordPress accounts. Try to provide unique passwords to reduce the chances of data breaching.
5. Wireless Sniffing

With the help of a sniffing attack, the attackers intercept data by capturing the user’s network traffic via a sniffing tool. These sniffer/snipping tools are effective for evaluating the user’s network packets. And, anyone can capture the wireless traffic if the network connection is not encrypted. Wireless sniffing helps the hackers to read the server data that is transferred between a suspected user and a client.
If you haven’t renewed WordPress’s SSL/TLS certificate, the attackers can use a sniffing tool to acquire the credentials. Most website developers recommend using a VPN while accessing any public Wi-Fi. Thus, attackers won’t easily capture nor read the WordPress information.
6. Password Cracking Methods

Do you know there are several passwords cracking techniques these cyber attackers use to assume a user’s WordPress credentials? Yes! Usually, they consider using three different password cracking techniques — brute force attacks, rainbow table attacks and dictionary attacks. Now, it’s time to figure out how these three methods help cyber attackers get WordPress credentials.
Brute Force Attack

In this technique, the attackers attempt different combinations of letters, numbers and characters to get the WordPress password. And, in most instances, they become successful in figuring out the right credentials. So, don’t provide passwords that anyone can guess easily; instead, provide something hard to decode.
Rainbow Table Attack

To crack the right password, the hackers sometimes use a rainbow hash table. They include certain mostly used WordPress passwords, common dictionary words, and a few pre-computed passwords in that table. In the majority of the WordPress security invasion cases, it was found that the users provided hashed passwords.
The potential attackers can easily identify certain types of passwords, which ultimately leads to data breaching. So, avoid using hashed passwords; and, to secure the website, try making it completely distinctive.
Dictionary Attacks
Source: https://thevpn.guru/
As its name implies, cybercriminals tend to use specific dictionary words in this type of password cracking technique. Sometimes, they mix up two different words to acknowledge the actual WordPress password. Though this method seems difficult, these potential hackers ended up guessing the right password in most cases.
Focus on Enhancing WordPress Security!
There are certain security measures that you can use to protect the WordPress site from cyber attackers. When it comes to WordPress security, locking the site is not enough. You have to invest in securing the WordPress host to avoid security issues. Every user should use the latest PHP version to secure the server. Make sure you are using the updated version of the application and have the current plugins and themes.

Locking down the WordPress admin section is another effective way to increase the site’s security. Limit the login attempts that will restrict an unauthorised person to access your WordPress site. And, no matter how secure the WordPress password is, consider using two-factor authentication.
Use HTTPS (HyperText Transfer Protocol Secure), and that’s the best security mechanism you can ever think of. And, if you need any help while implementing these security solutions, make sure to contact an expert.
